Rsync & CVE-2018-5764
Understand how Rsync works — and why missing --protect-args can lead to remote command execution.
What is Rsync?
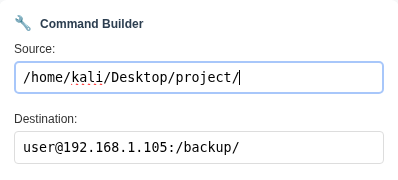
Rsync is a powerful utility for file synchronization between systems, commonly used for backups, mirroring, and remote transfers.
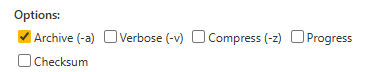
rsync -av /source/ user@host:/destination/-a: Archive mode
-v: Verbose output
CVE-2018-5764 Explained
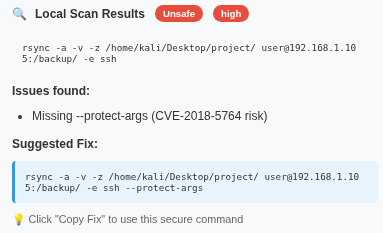
This vulnerability occurs when Rsync is executed without --protect-args. User input can be interpreted as shell commands on the destination server.
Danger: Remote command execution → full server control
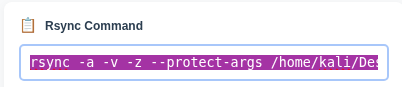
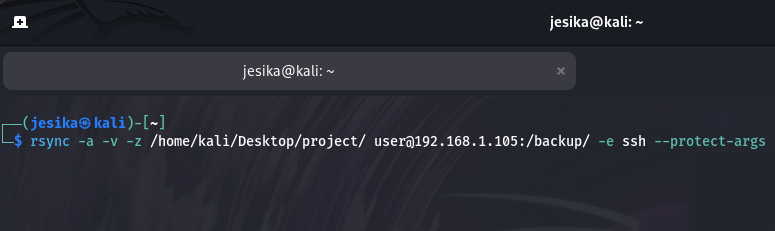
Unsafe Command
rsync -av /src user@host:/dest⚠️ Missing --protect-args → Risk of command injection
Secure Command
rsync -av --protect-args /src user@host:/dest✅ With --protect-args → Safe transfer
Network Diagram
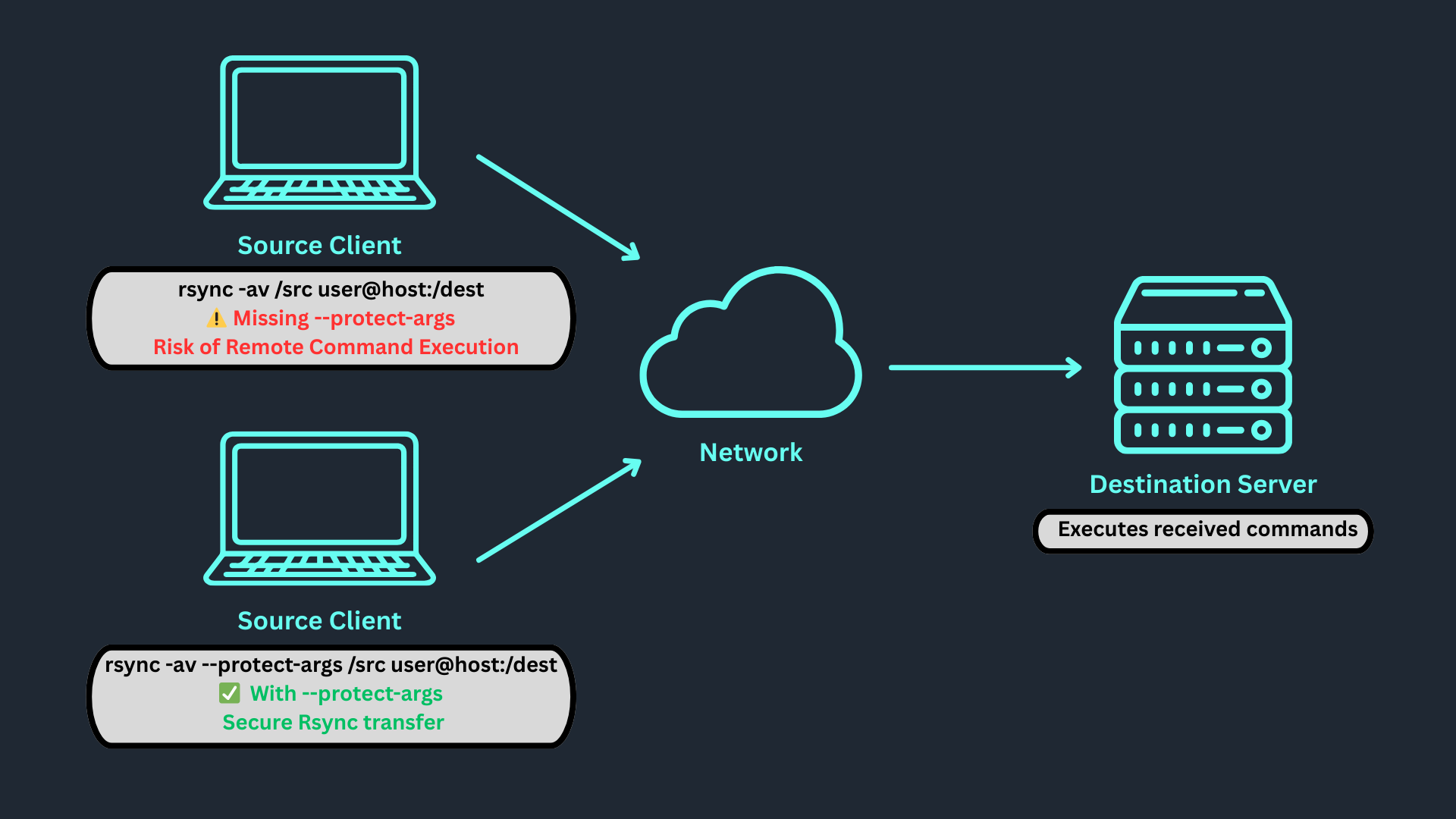
Source Client: Sends Rsync command
Network: Transmits securely via SSH
Destination: Executes received commands